‘Ethical hacking’ seems like a misnomer. Hacking into somebody’s account or service doesn’t seem very ethical – but you might be surprised by the good it can do.
Nowadays, with a bit of know-how and a connection to the internet, anyone can be a hacker, so here’s the lowdown on doing it ethically.
While most people will only ever deal with something like a password leak, being on the receiving end of a conventional hack is bad news. Ethical hackers, on the other hand, help to eliminate threats, as well as improving IT systems’ overall security.
Here’s everything you need to know about ethical hacking, why it’s becoming more important in modern life, and how to get started in the business.
What is ‘ethical hacking’?
First off, it’s best to forget anything learned about hacking from TV or movies.
Put simply, ethical hacking (or penetration testing) is the process of exploiting an IT system – with the owner’s permission – to determine any vulnerabilities or weaknesses. The results are then used to tighten online security for both the end user and the system owner.
Hackers normally operate within one of three categories which identify their intentions and methods: white hat, grey hat, or black hat. These terms derive from American westerns from the 1920s on, where white or black cowboy hats denoted goodies and baddies respectively. Grey, naturally, is somewhere in between.
- Black hat hackers tend to be the ones reported on by the mainstream media, as they seek to steal or modify data for illicit gains. They’re usually financially driven, although their primary motive can also be to cause havoc.
- White hat hackers are typically of the ethical variety. They look for exploits, and typically ask for permission before getting to work. If sending unprompted bug reports, they’re unlikely to release or sell the data even without a reward for their efforts.
- Lastly, grey hat hackers aren’t necessarily malicious, but will want some form of payment for finding an exploit. They probably won’t have permission from the website owner, but don’t really care. Their ambiguous nature means their behaviour will depend on individuals’ personal ethics.
Examples of ethical hacking
Since ethical hacking is seen as a good news item in the tech sector, you won’t have to look far for inspiring examples:
Lone Ethical Hackers

In 2019, the BBC ran a report about one Mark Litchfield, who has made roughly $1.5m finding bugs for companies like Yahoo. While the money is clearly alluring, most people are in it for the prestige, as well as recognition from other hackers in the industry.
Litchfield makes a point of noting that he can’t code, but the report did add that “he turned to bug hunting after years of working in the security industry, where he became an expert on the protocols that govern how computers swap data.”
In other words, he used his expertise to target a specific niche, and he’s been reaping the rewards ever since. Sometimes it’s better to not go in blind, and it’s hard to be effective without prior knowledge or willingness to learn.
He also helped to create Cyber Discovery with the UK government: a free, extracurricular online course “turning teenagers across the country into cyber security experts.”
Ethical Hacking Groups
There are many ethical hacking groups around the globe, whose members may not be from the same region. This is the beauty of the internet, and means you should be able to a group easily if you’re determined enough.
A group of ethical hackers from Adelaide recently won the National Missing Persons Hackathon, providing almost 100 new pieces of information, generating leads for 12 Australian missing-person cold cases.
A little closer to home, in York, November 2018, a hacker from Rapidspike found a flaw in a council app allowing personal data to be breached. The City of York Council floundered, contacting North Yorkshire Police and the Information Commissioner’s Office after the data breach was reported.
They tweeted, “Despite attempts to contact [the hacker], they did not respond and as a result of what appears to be a deliberate and unauthorised access we informed the police”.
Rapidspike issued a response defending the developer, as well as white hat hacking:
“It is important to note here that our developer did not do ‘anything to exploit the vulnerability.’ He simply browsed to a page within the app, as any user would. We’re releasing this statement in response to the reporting of the data breach and to help protect and encourage white hat security researchers who perform an absolutely critical role in the fight against cybercrime.”
The council eventually changed their tune, conceding that:
“It has become clear that the person who identified the issue with the app had tried to contact us but their email had not been received due to security settings. Whilst we consider we took appropriate measures based upon the facts at the time, we can now confirm that this was a well-intended action by the individual concerned and we would like to thank them for raising this matter.”
The point is, hackers don’t always receive a hero’s welcome, and it’s not unthinkable to receive a call from the police if there’s a failure of communication. Some organisations don’t like flaws being highlighted, and view any hacker as an aggressor. The council were likely trying to save face, especially as 5,994 accounts could have potentially been breached. It’s something to bear in mind for any would-be penetration tester.
Examples of Unethical Hacking
Conversely, there are numerous examples of unethical hacking, and everything from individuals’ emails to large companies have been affected in one way or another. Most fraudsters will use phishing or malware to achieve their goals, but others look for security flaws to gain entry into computer systems.
Here are a couple of big stories from the past few years involving either grey or black hat hackers, highlighting the damage they can do if undetected for a significant period. You’ll wonder why York’s council were so defensive when they got off lightly by comparison.
Ashley Madison, 2015

The Ashley Madison dating service is marketed to those who are married or in a relationship. They were hacked in 2015 by a group calling itself the Impact Team, who went after both Ashley Madsion and its owners, Avid Life Media. The hackers demanded that the service be shut down immediately, or they’d mass-release customer records.
The Impact Team ultimately released over 60GB of personal data, blaming Avid Life Media’s “deceptive practices”. The hackers were interviewed by Vice, in which they gave a semi-coherent response when asked why they did what they did:
“We were in Avid Life Media a long time to understand and get everything. Finally we watched Ashley Madison signups growing and human trafficking on the sites. Everyone is saying 37 million! Blackmail users! We didn’t blackmail users. Avid Life Media blackmailed them. But any hacking team could have. We did it to stop the next 60 million. Avid Life Media is like a drug dealer abusing addicts.”
It’s a poor excuse, especially considering the impact on users in countries where adultery is illegal, or when people began combing through the data to look for celebrities. Despite the website’s questionable morality, releasing such data was arguably a step too far. It’s a shade of grey at the very least, even if the hackers felt morally justified in doing so. (Don’t get me wrong, I don’t feel much sympathy for the company itself, but the choice of individuals to use the service is a whole other issue.)
Ashley Madison had made a number of questionable business decisions, from creating fake profiles to counterbalance their large male audience (70% of users), to keeping names, addresses, and credit card info indefinitely. (The latter was proved by the data dump, which included information about people who had quit the service years before.) However, the hack was a massive invasion of privacy, with users and their families consequently subject to numerous blackmail attempts over the next few years – though, conversely, the company is back to 30m users as of 2019.
An interview with chief strategy officer Paul Keable shed more light on the saga:
“What was fascinating, and unreported through the entire 2015 event, is that we were seeing sometimes upwards of 100,000 people sign up a day through the worst period of August 2015. And while some were curious ‘looky-looks’ or journalists, our revenues jumped double-digit against our weekly averages during that time frame. That showed us there was continued interest.”
In other words, the hack had minimal effect on the company in the long-term. Instead, users and their friends and family were often blackmailed, or had their lives ruined by the hackers’ activities.
Marriott, 2018
Large hotel chain Marriott was subject to a devastating hack which impacted up to 500m visitors to its Starwood hotels. As with Ashley Madison, having broken through online security the hackers spent up to five years collecting data.
While 170m Marriott customers had only their names and basic information like home address or email stolen, another 327m had varying combinations of name, address, phone number, email address, date of birth, gender, trip and reservation information, passport number, and Starwood Preferred Guest account information lifted.
That’s a dizzying amount of personal information, enough to give anyone affected the massive headache of identity theft due to the leak. The company was subsequently fined £99,200,396 by the Information Commissioner’s Office (ICO) for breaching the General Data Protection Regulation (GDPR), which also issued a statement;
“The GDPR makes it clear that organisations must be accountable for the personal data they hold. This can include carrying out proper due diligence when making a corporate acquisition, and putting in place proper accountability measures to assess not only what personal data has been acquired, but how it is protected.”
Marriott responded soon after, with a blog post expressing their intent to contest the fine. President and CEO, Arne Sorenson, stated:
“We deeply regret this incident happened. We take the privacy and security of guest information very seriously and continue to work hard to meet the standard of excellence that our guests expect from Marriott.”
That’s little consolation for the millions of users who could potentially be affected. In any case, most companies can’t afford to skimp on spending in order to protect online data. In the UK, the ICO is far from toothless, having the power “to impose […] fines of up to €20 million, or 4% of your total worldwide annual turnover, whichever is higher.”
It’s a significant amount, and another reason why white hat hackers are so important. Companies should be grateful if someone contacts them to highlight a flaw, as the alternative can be costly.
British Airways, 2018

You’d think British Airways would have robust online security, especially given the implications in a post-9/11 world. Nevertheless, experts say hacking the airline must have been a simple task, since the perpetrators required only 22 lines of code to steal credit card info from hundreds of thousands of BA customers.
If you’re interested in how it worked, “the malicious code grabbed data that customers entered into a payment form, and sent it to an attacker-controlled server when a user clicked or tapped a submission button.”
The hackers even paid for an SSL certificate to add legitimacy, and the airline was fined £183.39m in 2019, subsequent to a report by the ICO. They found that “personal data of approximately 500,000 customers were compromised in this incident.”
Once again, there’s a clear difference of intent by comparison to ethical hackers. As soon as they’ve found an exploit, malicious individuals will bed into the system to wreak as much havoc as possible. In the end, both the customer and the company lose out.
Why Ethical Hacking is Important
It’s easy to think of black and grey hackers as common cyber criminals, but that’s not always the case. While many of the examples above were likely the handiwork of small independent groups, there’s always a chance that their actions are being bankrolled by the state.
State-Sponsored Hacking
The stereotypical hacker is a lone wolf, interested in accessing systems and data because they want to investigate UFOs, or test themselves against some of the best security software on the planet.
In reality, state-sponsored hacking is a far bigger problem than the actions of individuals. Microsoft recently announced that they had notified almost 10,000 people targeted by state-sponsored hackers in the past year. They claim this shows the “significant extent to which nation-states continue to rely on cyberattacks as a tool to gain intelligence, influence geopolitics, or achieve other objectives.”
Most groups can be traced back to Russia, North Korea, and Iran, although it would be naive to think that the West don’t have their own online armies in operation. However, while their methods are likely to be similar, many state-sponsored hacks are carried out for financial gain.
Hacking can be a substantial source of income for poorer countries. For instance: the infamous WannaCry hack that infected and encrypted computers around the world for a couple of days in 2017, demanding that organisations like the NHS pay ransom in Bitcoin to unlock their data.
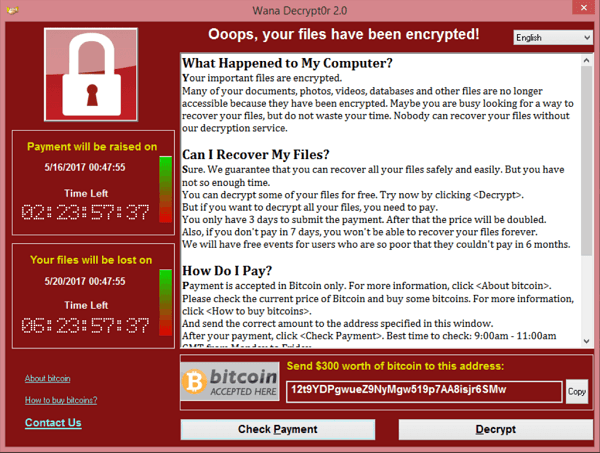
WannaCry is said to have originated from North Korea, although they deny any involvement officially. Bloomberg interviewed a former hacker from the country, who disclosed that he made roughly $100,000 per year by cloning software, as well as other more menial tasks.
“When orders were slow, he and his colleagues hacked gambling sites, peeking at the cards of one player and selling the information to another. They created bots that could roam around in online games […], collecting digital items like weapons and clothes and scoring points to build up their characters. Then they’d sell the characters for nearly $100 a pop. Every so often, to maintain the facade that he was pursuing research to benefit North Korea, Jong would create scholarly software, for example a data-graphing program, and send it across the border.”
For the North Koreans interviewed, money was the primary motivation, while others are interested in kompromat (“compromising material”).
White hat hackers are necessary to keep ‘the bad guys’ at bay, and they’re only going to get more sophisticated as countries ramp up their efforts in the constant information war. It’s not just network security, it’s also the wider concept of national security that is regularly put at risk.
Economic Espionage
By comparison to North Korea, China and Russia operate on a different level. In December 2018, much of the attention was on Russia following accusations that they’d interfered with the US election. It soon switched to China following a press conference by the FBI and the US Justice Department. Two Chinese nationals were labeled spies and charged with stealing confidential data from American government agencies and international businesses, leading FBI Director Chris Wray to say:
“No country poses a broader, more severe long-term threat to our nation’s economy and cyber infrastructure than China. China’s goal, simply put, is to replace the U.S. as the world’s leading superpower, and they’re using illegal methods to get there.”
Since many countries hack and spy on each other to some degree, white hat hackers can have a positive effect by ensuring IT systems are up to date and secure.
Meanwhile, Russia has been accused of hacking the US election, a global chemical weapons watchdog, Internet of Things devices, and everything and anything in between. If you want a full list check out these Significant Cyber Incidents collated by the Center for Strategic and International Studies, hit control F, and type “Russia”.
Hackers need to be highly skilled, and many countries have the resources to use these individuals to identify and carry out sustained attacks on any vulnerabilities they find. It’s little wonder the UK government is pushing forward with plans like Mark Litchfield’s Cyber Discovery programme. They’re hoping to inspire the next generation, while being open about the potential to “defend the internet from attacks and keep your country safe from cyber terrorists”.

How to Become an Ethical Hacker
It’s clear why ethical hacking has become significant, but how and why would you do the job in the first place? Incredible financial perks tend to help. The council probably won’t be forthcoming with moolah, but at the Black Hat Briefings security conference in Las Vegas, Apple announced they’d pay ethical hackers over $1m for responsibly disclosing dangerous security vulnerabilities. After all, that’s preferable to hackers selling information on to third parties, which would see Apple’s reputation taking a hit when users are inevitably caught up in the fallout.
However, though online courses are ten-a-penny, they aren’t necessarily worth the asking price. You’d arguably be better off teaching yourself about IT systems and security, or getting involved with an online community. Holly Duncalf was responsible for talent identification and acquisition for NCC Group’s ethical hacking division in the UK back in 2016, and she gave some helpful advice to anybody who is aiming to get started. ike Mark Litchfield, she stressed that:
“You don’t simply become an ethical hacker overnight Matrix ‘I Know Kung Fu’-style. We find those who excel at ethical hacking are those for whom it is a true vocation that blends with a general interest in science, technology, engineering and mathematics. Developing the skills and keeping up to date is hard work, however, [so] if you aren’t afraid of that, are tenacious, enjoy problem solving and critical thinking you are likely well-suited.”
Of course, a background in IT would be highly beneficial, while a degree in maths or physics would definitely help. For those with none of the above, vocational courses like City & Guilds in software development will prepare you for life as an ethical hacker.
Duncalf also mentions that it’s a good idea to learn a programming language such as Python, Go, C#, Objective C, Java, or C, as this should provide a better understanding of the systems you’re trying to find flaws in.
Above all, everybody has to start somewhere, and initially you only need a keen interest and a willingness to learn. You could focus on a specific platform like Linux, but you can also learn more about penetration testing via the classroom.
If you’d prefer to go down the certification route, here are some options:
Becoming a Certified Ethical Hacker (CEH)
You don’t have to be certified to become an ethical hacker, although there are a number of courses and opportunities available online and across Britain. It makes sense to learn more, if possible, and you’ll likely find it easier to get started after some training in the profession.
Abertay University is the first in the UK to offer an undergraduate course in ethical hacking, although they did drop out of the top 100 in the country’s rankings for 2020. Regardless, it’s a specialised niche, and more courses are likely to be started in universities around the world. It’s not a bad real-world option.
The Abertay course “combines computer networking, digital forensics and expert development as well as programming. You will learn how to protect data and information systems.” It’s also accredited by the Chartered Institute for IT. Overall, it’s reasonably extensive, and covers many of the different aspects discussed above by the experts. It’s ideal if you don’t know what a honeypot is, or if you think a SQL injection is something you’d get from the doctor. (Sorry, I’ve been watching too many Weakest Link reruns.)
The point is, you’ll develop a valuable set of skills, as well as learning more about different ethical hacking tools.
You can also check out CREST: an international not-for-profit accreditation and certification body that represents and supports the technical information security market. A UK branch was established in 2016; a number of examinations are available here and worldwide, and you can find out more about fees here.

As the importance of ethical hacking grows, further opportunities in terms of training and work are likely to arise. For now, the options are varied enough to get started if you know where to look, and you could be improving operating systems in no time.
Lastly, there are lots of uncertified courses out there, with people hoping to cash in on an excess of would-be hackers online. It’s best to be wary if you’re looking on Google, as scam artists are unlikely to give you the lowdown on how to be a good ethical hacker.
Make sure courses are backed by security professionals such as CREST or the EC-Council, while the Certified Ethical Hacker certification is the industry standard. I’d personally opt for CEH certification, although any of the legitimate options I listed seem like a good choice! It’s the easiest way to learn about everything from seeking out common backdoors, to footprinting computer systems for extra info like a pro. You could make a real difference if you manage to stop a malicious hacker.
Resources and further reading:
We’ve come up with a list of resources if you’d like to learn more about ethical hacking, as well as more information about where you can learn to become a white hat-wearing tech wizard. We’d also appreciate any suggestions or tips you may have for budding ethical hackers! We’ll be sure to add them to the list.
From system hacking to intrusion detection, here are a few good places to start.
- Cyber Discovery
- ‘Looking for a Career in Ethical Hacking in the UK – Part One – Where to Start…’
- Cyber Security Challenge UK
- Significant Cyber Incidents
- National Crime Agency: Cyber Crime
- TED Talk: Caleb Barlow: ‘Where Is Cybercrime Really Coming From?’
- EC Council
Featured image by Markus Spiske on Unsplash



Leave a Reply